

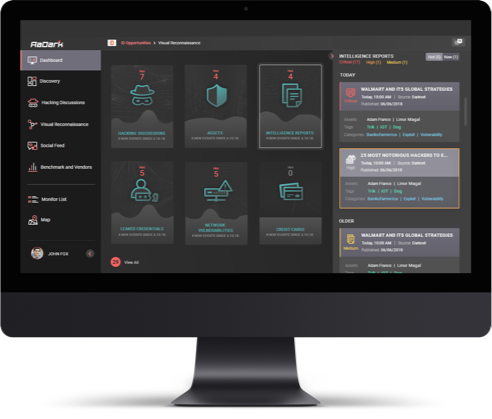
KELA’s process of gathering and analyzing data emulates the thought-process of a hacker prior to an attack
While KELA's technologies monitor intelligence in more than 100 languages, our team speaks a total of more than 20, all common in Darknet communities
Our analysts scan and handpick new information sources daily, ensuring all potential threats are being monitored
Highly targeted intelligence-gathering prevents any generic, redundant or low-impact threats
Immediate notifications and 100% actionable alerts of Darknet threats
Integrating automation and manual oversight by analysts guarantees the most relevant intelligence analysis and remediation process
מולטיפוינט גרופ, היא המפיצה של פתרונות הגנת סייבר מובילים לאנטרפרייז, לעסקים קטנים ובינוניים, ול- MSP וספקי שירותים.
תשלום מאובטח באמצעות:




