Bitdefender GravityZone עובד לרוחב נקודות קצה ועומסי עבודה היברידיים, עם אנליטיקה יעילה, יכולות אבטחה מרובות, וניהול קל לתפעול
טכנולוגיית מניעת ההתקפות של Bitdefender ומודלים ללימוד מכונה מזהה ועוצרת יותר התקפות עוד לפני שהן מתחילות
שקיפות מלאה לגבי אבטחה לרוחב תחנות עבודה, שרתים מקומיים, סביבות וירטואליות ועומסי עבודה בענן. אנליטיקה לרוחב נקודות קצה שונות מאפשרת לזהות טווח רחב התקפות מתקדמות.






– זיהוי ותגובה מורחבים (XEDR) מראים בדיוק כיצד איום פוטנציאלי פועל בסביבה שלך
– טכניקות MITRE וסממני פריצה מספקים תובנות מעודכנות ברמת הדקה לגבי איומים מוכרים וקוד זדוני שעלולים להיות מעורבים בהתקפה
– תצוגה ויזואלית מציגים בקלות אפיקי תקיפה חיוניים, ומקלה את העומס על צוות ה- IT
– המלצות חכמות לתגובה מספקות לצוות צעדים לתיקון ולמזעור מישור התקיפה
– דאשבורד המציג סיכון לרוחב כל הארגון
– תיעדוף הסיכון של בעיות בהגדרות, אפליקציות, ופגיעויות שיצרו משתמשים לרוחב נקודות הקצה בארגון
– צילום מצב של שרתים ומכשירי קצה, וסקירה של נקודות הקצה והמשתמשים החשופים ביותר
– התבייתות על בעיות בהגדרות, פגיעויות באפליקציות, סיכונים בהתנהגות משתמשים, מכשירים, ותיקון בעיות או עדכון פגיעויות.
ההגנה המשולבת של GravityZone מובנית לתוך הפלטפורמה במספר רמות, עם הגנה עדיפה על פתרונות אבטחה מתחרים
– שכבות חסימה מרובות להגנה על נקודות קצה ורשת, הפעלה מוקדמת (pre-execution), והתקפות ללא קבצים
– שכבות זיהוי מרובות בוחנות תהליכים, מנטרות את הרג'יסטרי, ובודקות קוד
– שכבות התאוששות מרובות מאפשרות Rollback ממכונה מקומית, מערכת מרוחקת או אירוע EDR
– הגנה אדפטיבית מתקדמת מבוססת לימוד מכונה
– גיבויים חסינים לפגיעה, כדי למזער את הפגיעה של התקפות כופר
– חסימה של תוכנות כופר וחסימת IP של התוקף
– ניקוי לרוחב הארגון של תהליכים, והסגר גלובלי ונוח של קבצים
עברייני הסייבר הופכים למתוחכמים יותר בכל יום, והקושי לזהות התקפות מתקדמות רק הולך ועולה. העבריינים מפעילים טכניקות הפעלה שבנפרד נראות כמו התנהגות רגילה של מערכות, וכך הם יכולים להישאר מוסתרים במשך חודשים – במהלכם הנזק המצטבר של הפירצה רק הולך וגדל.
סנכרון מידע ממכשירים שונים
יכולות הזיהוי והתגובה של Bitdefender EDR מרחיבות את יכולות האנליטיקה והקורלציה של אירועים כדי לכלול נקודות קצה שונות, ומאפשרות לזהות מתקפות מתוחכמות.
הטכנולוגיה לקורלציה בין נקודות קצה שונות, משלבת את הירידה לפרטים והמידע העשיר של ה- EDR לצד האנליטיקה הרוחבית של ה- XDR.
עם היכולת להציג בצורה נוחה את האיומים ברמה הארגונית, ה- XEDR מאפשר לך למקד את החקירה ולהגיב בצורה יעילה יותר.
ה- EDR זמין בפתרון עצמאי המשלים את פתרון הגנת נקודות הקצה הקיים או כחלק מפלטפורמה מלאה להגנת נקודות קצה
יישום קצה, קל להפעלה, עם ניהול מהענן
אנליטיקה ייחודית של משתמשים ונקודות קצה מספקת עצות מעשיות לשיפור מצב האבטחה ולמזעור סיכונים
פלטפורמה גמישה וסקלאבילית לניהול כל נקודות הקצה ולתגובה וזיהוי מנוהלים
תהליכי תגובה מובנים וקלים למעקב מאפשרים לצוות להגיב ביעילות, ולהגביל את יכולת התנועה הרוחבית של תוקפים
ויזואליזציה של איומים ברמה הארגונית, ממקדת את מאמצי החקירה ומסייעת לך להבין את זיהוי מורכב, לזהות את מקור ההתקפות, ולהגיב במהירות.
תיעדוף אוטומטי של התרעות עם יכולות פתרון בלחיצה אחת
זיהוי איומים מתקדמים שמאפשר ליהנות מהחוזקות של XDR בהגנת נקודות קצה
נראות מלאה לגבי טכניקות, טקטיקות ותהליכים (TTPs) המשמשים כדי לתקוף את המערכות שלכם
יכולות חיפוש מקיפות אחר סממני תקיפה (IoCs), טכניקות MITRE ATT&CK וממצאים נוספים היכולים לחשוף התקפות בשלבים המוקדמים שלהם.

קביעת רמת הסיכון – ניתוח רציף של הסיכון של אנשים ונקודות קצה על פי מאות גורמים, כדי לחשוף ולתעדף סיכונים בהגדרות של כל נקודות הקצה.
דאשבורד בזמן אמת – מספק תובנות לגבי מצב האבטחה של סביבת המחשוב שלך.
דוחות מקיפים – מספקים לך את המידע הנדרש כדי למדוד השפעה על הפעילות העסקית.
התראות – באמצעות דאשבורד ודואר אלקטרוני.
אינטגרציה של SIEM ו- API – כולל אינטגרציה עם Splunk וכלים אחרים.

חיפוש סממני פריצה (IoC) – הרצת שאילתה מול בסיס נתוני האירועים מאפשרת לחשוף איומים. ניתן לחשוף טכניקות MITRE ATT&CK וסממנים לפריצה. תובנות מעודכנות ברמת הדקה לגבי איומים מוכרים וקוד זדוני אחר שעלול להיות מעורב בהתקפה.
ויזואליזציה ברמת הארגון – תצוגה ויזואלית קלה להבנה מציגה פעולות עוינות, מועשרת בנתונים, לצד מודיעין איומים. הדבר מקל על זיהוי אפיקי תקיפה קריטיים ומוריד עומס מה- IT.
פירוק איומים – מחקר בארגז חול מסייע לך לקבל החלטות לגבי קבצים חשודים.
רשימות שחורות – חסימה של התפשטות קבצים חשודים או תהליכים שזוהו על ידי EDR או מערכת אחרת.
חיסול תהליכים – חיסול מיידי של תהליכים חשודים לעצירת פריצות בזמן אמת.
ניתוק רשתות – חסימת קישורים אל ומתוך נקודות קצה כדי למנוע תנועה רוחבית ופריצות נוספות במהלך החקירה.
Remote Shell – הפעלת פקודות מרחוק על כל תחנת עבודה כדי להגיב מיידית לכל אירוע.

XEDR – יכולות זיהוי ותגובה מורחבות – טכנולוגיה המספקת קורלציה של אירועים כדי לספק רמה חדשה של שקיפות. הטכנולוגיה מפעילה יכולות XDR לזיהוי התקפות מתקדמות הכוללות מגוון נקודות קצה בתשתית היברידית (תחנות עבודה, שרתים, וקונטיינרים – תחת מערכות הפעלה שונות)
אנליטיקה של איומי סייבר –
איסוף של נתונים בענן מאפשר לזקק את האירועים החשובים ביותר, עם תיעדוף לצורך תחקור וניתוח.
מקליט אירועים – ניטור אירועים רציף בנקודת הקצה, מזין אירועים אל האנליטיקה כדי לייצר ויזואליזציה של האירוע.
Sandbox Analyzer – הפעלה אוטומטית של מטענים חשודים בסביבה וירטואלית אטומה. מודול האנליטיקה משתמש בניתוח הזה כדי לקבל החלטות לגבי קבצים חשודים.
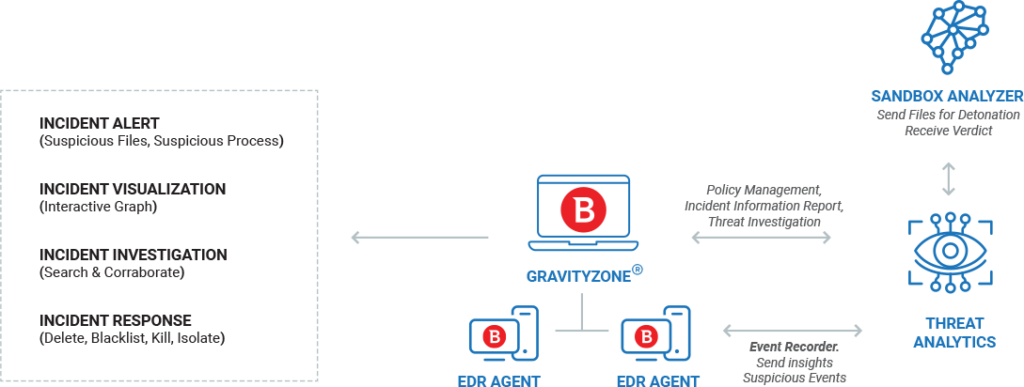
Bitdefender EDR הוא פתרון שנבנה לענן, עם תמיכה מלאה בהפעלות מקומיות. יישומי קצה (סוכנים) מותקנים בכל נקודות הקצה של הארגון. לכל סוכן EDR יש מקליט אירועים שמנטר באופן רציף את נקודת הקצה ושולח תובנות ואירועים חשודים לפלטפורמת GravityZone.
ב- GravityZone, מודול האנליטיקה אוסף ומזקק את האירועים מנקודות הקצה לרשימה של אירועים עם תיעדוף. הוא שולח קבצים חשודים לניתוח ב- Sandbox Analyzer, ואז משתמש בתוצאות בדוח האירוע.
ניתן לגשת ללוח הבקרה בזמן אמת של ה- EDR מכל מכשיר כדי לאפשר לאדמינים לראות התראות וגרפים, ולאחר מכן לחקור ולהגיב בהתאם.
מולטיפוינט גרופ, היא המפיצה של פתרונות הגנת סייבר מובילים לאנטרפרייז, לעסקים קטנים ובינוניים, ול- MSP וספקי שירותים.
תשלום מאובטח באמצעות:




